Here are the most common challenges faced by many organizations today in relation to privileged accounts:
All PAM systems are designed specifically to meet the complex and growing security and compliance requirements associated with privileged identity management and privileged access controls within the enterprise. The focus of the solution is to provide the enterprise a cost-effective modular platform from which they can enable various privilege control functions as required based on current and/or future privileged access control requirements. The proven approach is to vault sensitive credentials in a secure appliance where the issuance of these credentials can be controlled or restricted entirely. By using PAM as a session proxy, users can be signed on to end systems with privileges, without ever knowing the password.
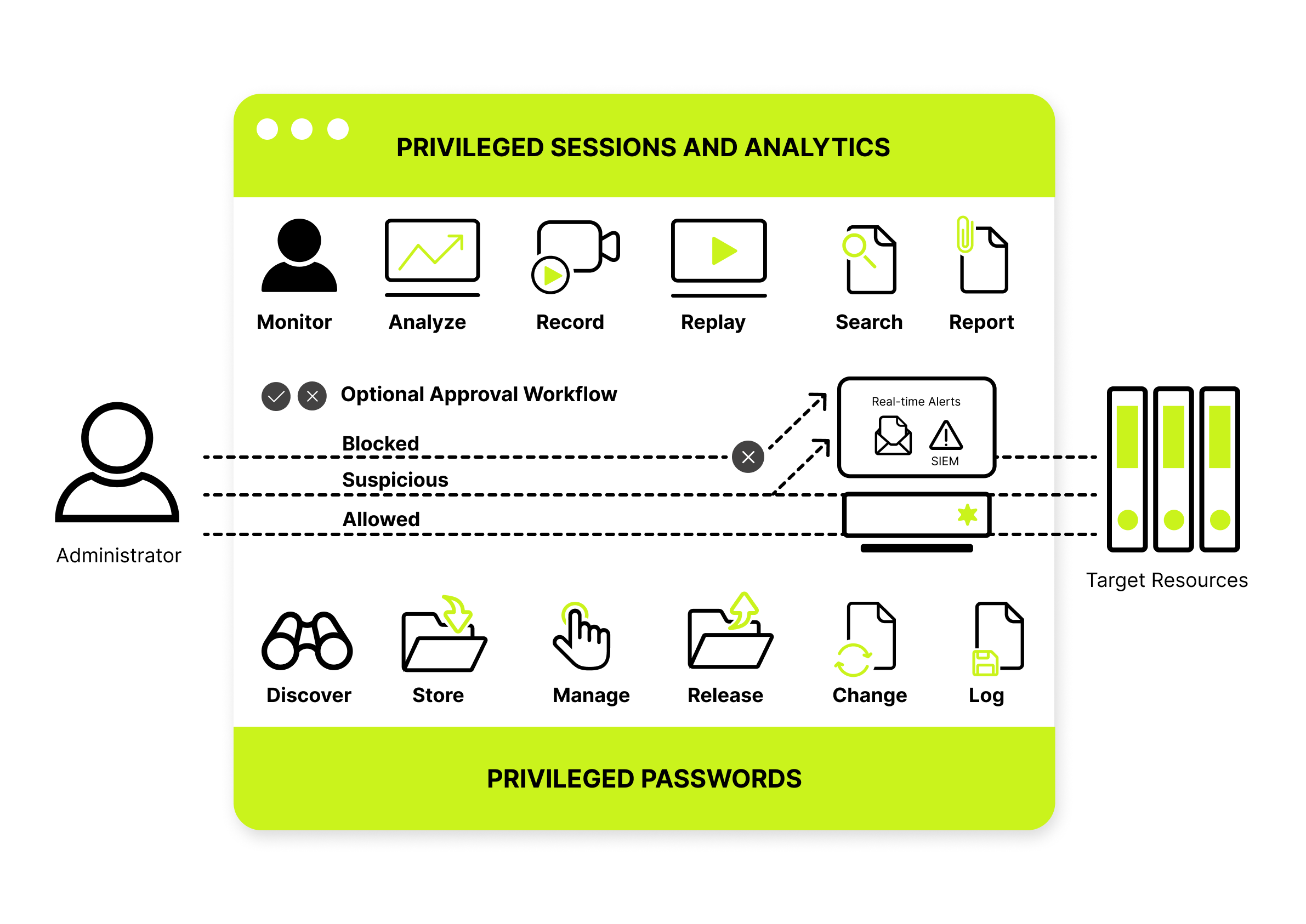
PAM solution offers two key functional areas for managing privileged access:
| PASSWORD MANAGEMENT | SESSION MANAGEMENT |
|
|
Reach out to UDV Tech to discuss your unique case and requirements. We have completed multiple successful PAM projects with businesses of all industries and sizes and earned One Identity trust and customer respect for going above and beyond in every project we tackle.
