Cybersecurity is everywhere. From personal devices and smart things to national industrial infrastructures and everything in between. Businesses require relevant and precise information concerning their security posture and ways to improve it, while facing multiple cybersecurity challenges:
- Remote working has become the norm
- More and more information is being processed in cloud services
- Malicious tools have become more accessible to adversaries than ever before
- The rise of hacktivism
Penetration testing is the only way to assess Company’s security posture and its ability to predict, prevent and respond to fast-evolving cyber threats. Penetration testing allows to run a real check on implemented security measures performance and employees’ awareness, to identify gaps in information security and demonstrate the compliance with the security requirements.
Security assessment objectives:
- Assess the current security posture
- Obtain a relevant list of vulnerabilities and threats
- Demonstrate existing security flaws
- Develop the action plan for high-priority security issues
Security Assessment tasks:
- Discovering information systems vulnerabilities
- Developing guidelines for discovered vulnerabilities remediation
- UDV Technologies provides a complete portfolio of pentesting services
| External vulnerability assessment and penetration testing (VAPT) focuses on gathering information about the company's IT infrastructure accessible from the Internet and includes discovery of all available resources and vulnerability detection in Customer’s applications, operating systems, and network infrastructure. For web applications, the service focuses on the software and configuration vulnerabilities. |

|
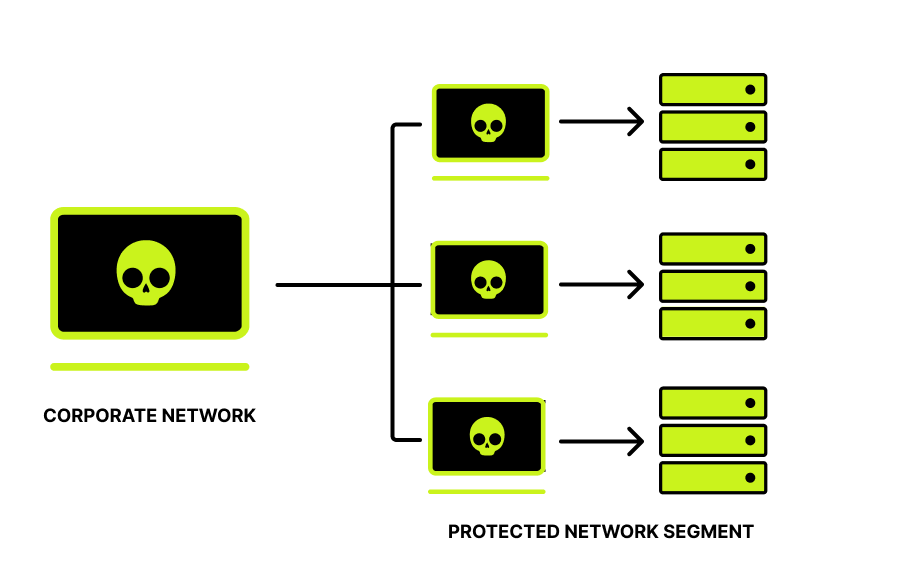
| Internal VAPT is focused on gathering information about corporate networks, employees’ personal computers, servers and IT infrastructure. This information is further used for analyzing the attack opportunities available the adversary from inside the corporate network |
|
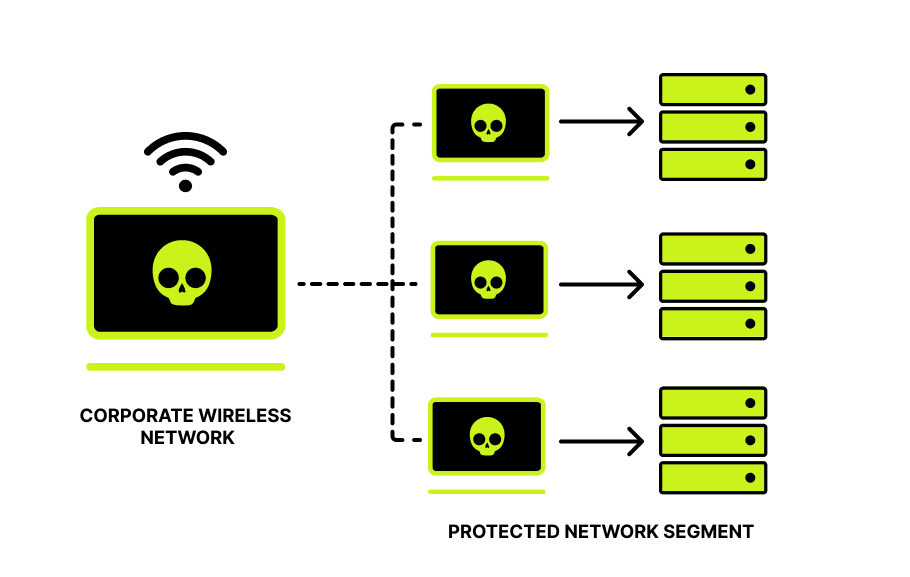
| Wireless networks security audit is focused on the wireless segment, modeling adversary actions using access to company’s wireless networks. It also includes detection of every access method to the infrastructure. |
 |
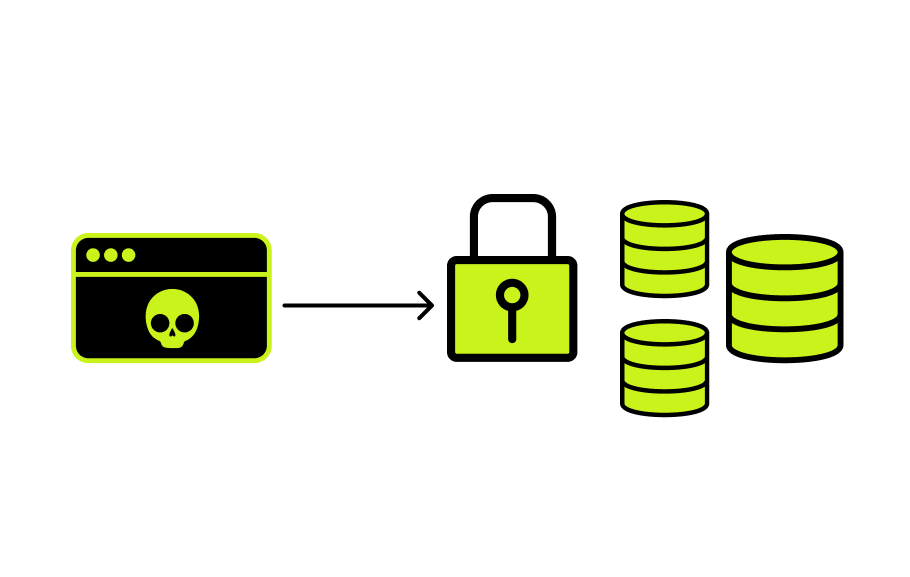
| Web application security analysis is a complete inspection of the web-application features in order to detect vulnerabilities introduced during application development. This service may also include web-application and mobile application source code analysis. |
|
| Load/stress testing is used for analyzing the system response time under high and peak loads. It includes DOS attacks emulation and assessments of their impact on the system performance. |
|
| Social engineering penetration testing utilizes various social engineering techniques including phishing. Results include users’ behavior analysis and security awareness assessment regarding applied social engineering methods. |
|
