Access Management
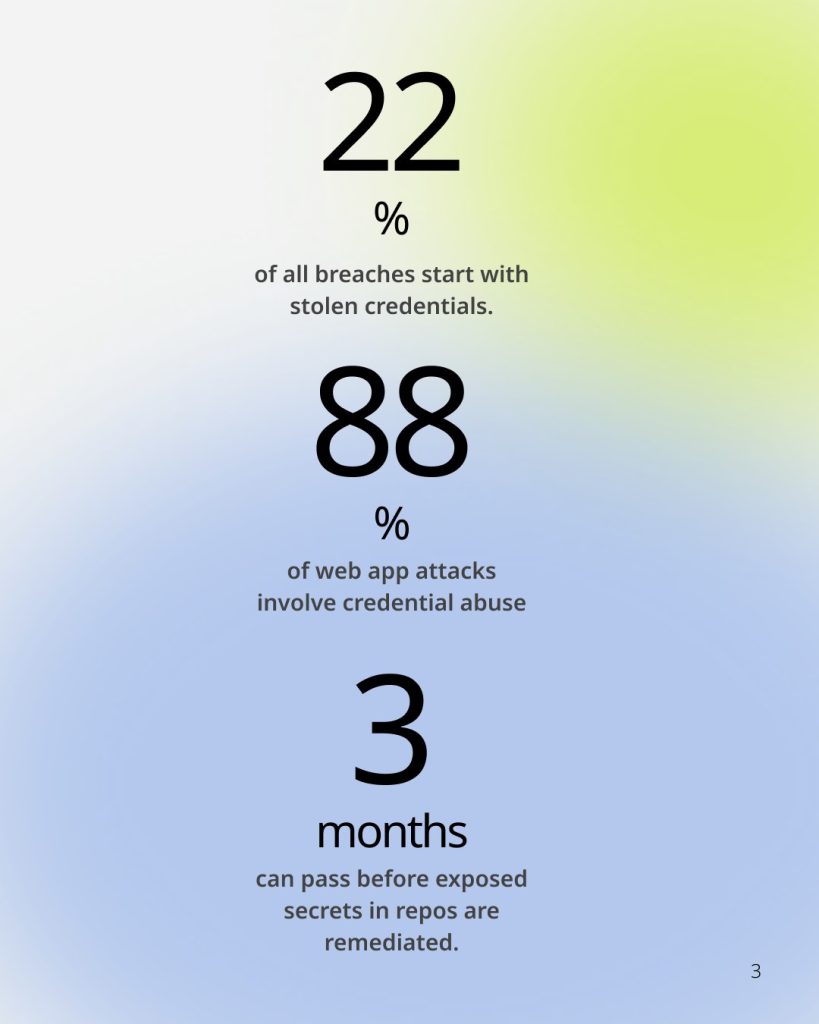
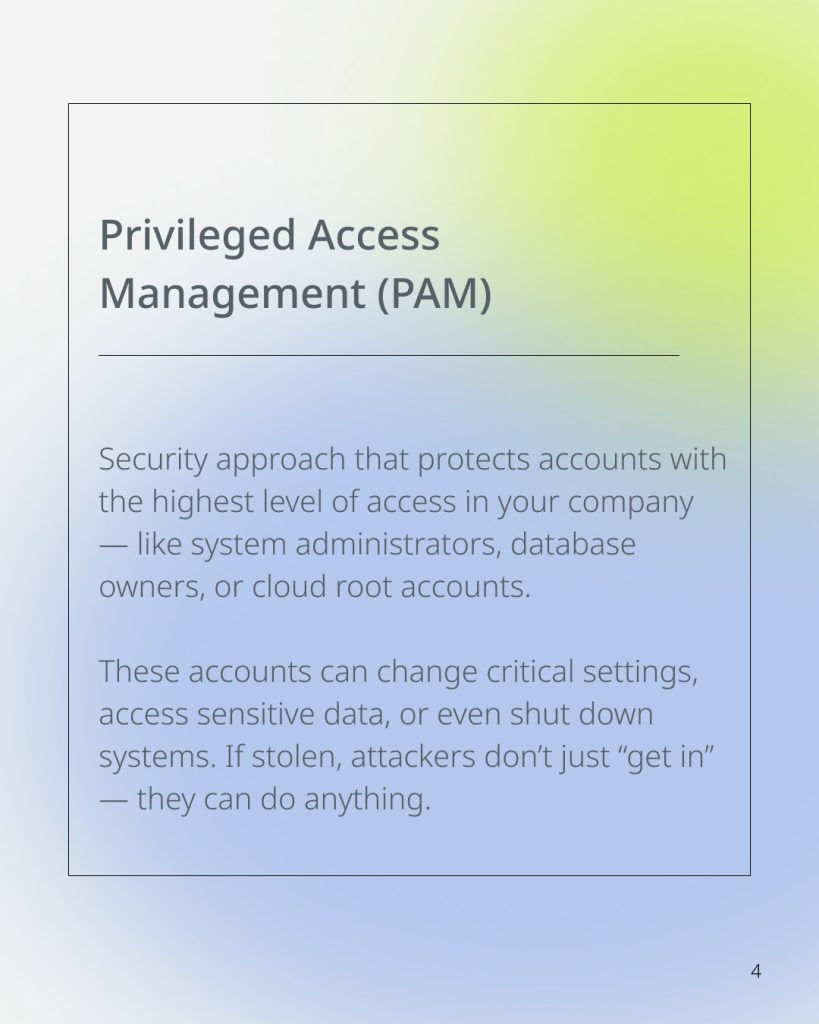
We break down fresh statistics how often cyberattacks start with stolen credentials and why access management (IAM, PAM) is the key to stopping them. We also explain what PAM is and how it protects the most powerful accounts in your business.